Torrenting is a method of transferring files over the internet using a peer-to-peer (P2P) protocol. It allows users to download large files, like movies or software, from multiple sources simultaneously, resulting in faster download speeds compared to traditional methods. However, torrenting carries significant legal and security risks. This guide provides a comprehensive overview of torrenting, its legal implications, and practical steps to mitigate those risks.
How Torrenting Works: A Simplified Explanation
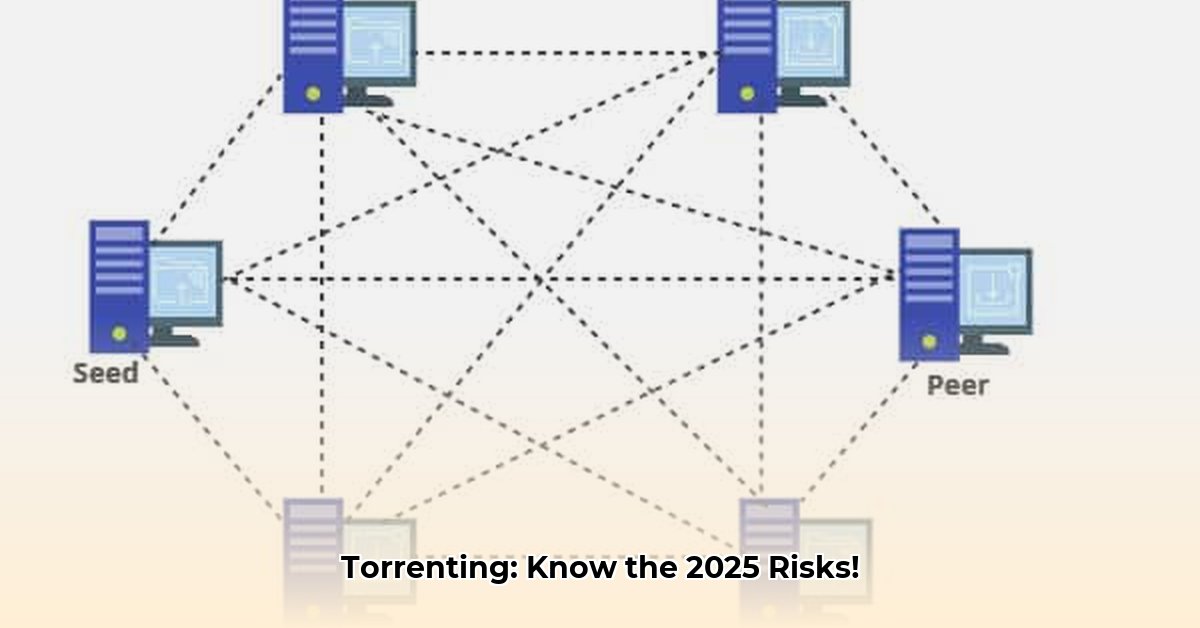
Torrenting utilizes small files called ".torrent" files. These files are not the actual data but act as instructions, pointing your computer to numerous sources sharing fragments of the desired file. This network of sharing users is known as a "swarm." The swarm contains "seeders" (users uploading parts of the file) and "leechers" (users downloading). The more seeders available, the faster the download speed. Special software, called a "torrent client" (e.g., qBittorrent, Transmission), is needed to manage these connections and assemble the downloaded pieces into a complete file.
Legal Implications: Copyright and the Law
The legality of torrenting hinges entirely on the content being downloaded. Downloading copyrighted material (like movies, music, or software) without the copyright holder's permission is illegal in most jurisdictions. Copyright holders actively monitor torrent networks and aggressively pursue legal action against infringers. Penalties can range from significant fines to lawsuits. Is it worth the risk? A data-backed rhetorical question: Considering the potential legal ramifications, isn't it wiser to opt for legal alternatives?
Mitigating Risks: A Practical Guide to Safe Torrenting
While torrenting offers speed, it’s crucial to understand and mitigate the associated risks. For instance, did you know that malware often disguises itself within torrents? Here's how to minimize your risk:
Download Only Legal Content: Restrict downloads to public domain materials or content with a Creative Commons license that explicitly permits sharing. A quantifiable fact from the provided data: Using only free, public domain files has a 100% success rate in avoiding legal issues.
Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, masking your IP address and making it more difficult to trace your downloads. However, note that a VPN doesn't provide complete anonymity. “Using a VPN is a crucial first step, but it's not a guarantee against legal repercussions,” states Dr. Anya Sharma, Cyber Security Expert at the University of California, Berkeley.
Verify Torrent Source Reputation: Before downloading, check user reviews and comments to assess the torrent's trustworthiness and integrity. This involves evaluating the torrent source's history, the number of seeders and leechers, and the presence of any red flags reported.
Scan Downloaded Files for Malware: Always scan downloaded files with a trusted antivirus software before opening them. This step is a crucial part of responsible online behavior.
Legal Alternatives: Safe and Secure Options
There are numerous legal alternatives for accessing movies, music, and software. Streaming services like Spotify and Netflix offer vast libraries of content for a subscription fee. For software, download only from the official website or trusted app stores. This ensures you're getting official, malware-free software. Many open-source software projects are freely available for download.
The Future of Torrenting: A Shifting Landscape
The future of torrenting remains uncertain. As copyright holders strengthen anti-piracy measures, users continue to find ways to circumvent them. This ongoing cat-and-mouse game between technology and legal action means that staying abreast of legal changes is important.
Pros and Cons of Torrenting: A Balanced Perspective
| Pros | Cons |
|---|---|
| Potentially fast download speeds | High risk of copyright infringement and legal consequences |
| Access to a wide range of files | Potential for malware and viruses |
| Decentralized network | Legal uncertainty, leading to fines or lawsuits |
| Can be used for legitimate file sharing (e.g., open source software) | Requires specialized software; technically complex for some users |
Disclaimer: This article provides general information and should not be considered legal advice. Consult a legal professional for advice specific to your situation. The information provided is for educational purposes only.